Investigating Overall Structure of Cyber-Attacks on Smart-Grid Control Systems to Improve Cyber Resilience in Power System
By Mohammad Ghiasi, Moslem Dehghani, Taher Niknam, and Abdollah Kavousi-Fard
Abstract: The use of information and communication technologies and computer-based software to enhance the quality, efficiency, and reliability of smart grids (SGs) have brought unwanted threats in these systems; one of the most important of such threats is cyber-attack. Understanding the ways to detect and deal with cyber threats in SGs will increase the resilience of power systems. In this paper, conceptual models of SG vulnerabilities are presented to address the issue of the vulnerability of SG control systems against cyber-attacks. Different scenarios of cyber-attacks are then dealt with in SG control systems to enhance their resilience.
1- Introduction
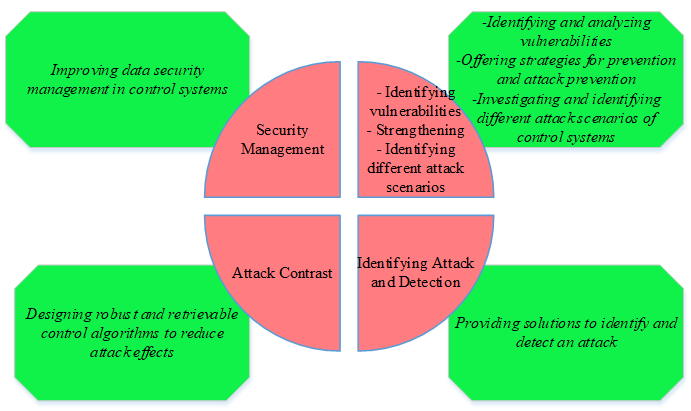
The main security issues of SG control systems against cyber-attacks are given in Figure 1. These issues are divided into four categories:
- Identifying different vulnerabilities and scenarios for attacking SG control systems and trying to prevent it
- Providing strategies to detect and identify the attack
- Recombining and using control tools to reduce the effects of the attack and increase the system's self-healing properties
- Improving cyber security management in SG control systems
Figure 1. The main security issues of SG control systems against cyber-attacks
2- Conceptual Model of Control Systems Vulnerabilities in Smart Grid
Controlling of SG in energy systems has the task of directing and controlling physical processes. They usually consist of a set of multiple components including sensors, operators, data processing units such as programmable logic controllers (PLCs), communication networks, and central computers. There are several general models for elucidating the structure of smart control systems [1, 2]. A conceptual model of SG control system vulnerabilities is presented in Figure 2. As can be seen from the Figure 2, the vulnerabilities of the SG control system are divided into six categories:
- Field equipment vulnerabilities
- Field equipment communication network vulnerabilities
- Local controller vulnerabilities such as remote terminal units (RTUs) and PLCs
- Vulnerabilities of control network communication protocols
- Local area network (LAN) control vulnerabilities
- Vulnerabilities of cooperative and financial-commercial networks
Figure 2. Conceptual model of SG control system vulnerabilities
The layered structure of this conceptual model emphasizes that the types of vulnerabilities of each layer of SG control system are different, and therefore each layer requires different security measures.
3- Identify Different Vulnerabilities and Scenarios of Cyber-Attack in Smart Grid Control Systems
With the advancement of control and protection systems in SGs as well as their use of the same software, hardware and network platforms and having the same standards, it is possible for unauthorized persons to access the internal layers of these systems. In general, an attacker who intends to attack a cyber-attack and damage an intelligent control system faces two major challenges:
- Identifying, penetrating and accessing the system
- Taking full or partial control of the process and damage it
So the first step in securing smart grid control systems is to identify vulnerabilities and access points. It can be divided into two major areas of communication equipment and protocols. The devices used in smart grid control systems also fall into two categories:
- Equipment used solely for control systems, such as sensors, actuators, RTUs, and PLCs
- IT equipment used in other systems and networks such as switches and computers
In this section, we first discuss a number of articles addressing the vulnerabilities of communication protocols of the SG control system and their solutions. Then, considering the extent of equipment vulnerabilities and articles in this field, first class equipment vulnerabilities are discussed. Finally, four categories of scenarios for attack on control systems in SGs are investigated.
3-1- Communication vulnerabilities and attempts to prevent intrusive influence
Nowadays, many protocols are used in intelligent control systems. Most of these protocols are designed to increase efficiency, reliability in real-time operations, and support for economic and operational requirements. Unfortunately, most of these protocols have ignored any unnecessary security features such as authentication and cryptography to enhance performance. Many have been developed by others to use the Ethernet protocol and connect to the Internet.
Therefore, the communication protocols of industrial control systems are very vulnerable and exposed many attacks [3]. According to the American Gas Association reports, there are about 150 to 200 supervisory control and data acquisition (SCADA) protocols. The integration of these protocols in recent years has resulted in the attackers obtaining very accurate information on their function and structure. In this way, attackers can identify and modify data packets by identifying vulnerabilities in these protocols [4]; like the attack on Queensland's Australian Water and Wastewater Control System in 2000 when an attacker was able to infiltrate the field's communications network and bring 800,000 liters of sewage into the city's safe water cycle by having complete information about the attacking protocol.The vulnerabilities of these protocols have been investigated in several sources. References [3, 5] discuss a variety of industrial protocols, their vulnerabilities and security solutions. One of the issues discussed in this source is the Modbus protocol that lacks authentication, encryption, and encryption integrity.Therefore, the communication protocols of industrial control systems are very vulnerable and exposed many attacks [3]. According to the American Gas Association reports, there are about 150 to 200 supervisory control and data acquisition (SCADA) protocols. The integration of these protocols in recent years has resulted in the attackers obtaining very accurate information on their function and structure. In this way, attackers can identify and modify data packets by identifying vulnerabilities in these protocols [4]; like the attack on Queensland's Australian Water and Wastewater Control System in 2000 when an attacker was able to infiltrate the field's communications network and bring 800,000 liters of sewage into the city's safe water cycle by having complete information about the attacking protocol.The vulnerabilities of these protocols have been investigated in several sources. References [3, 5] discuss a variety of industrial protocols, their vulnerabilities and security solutions. One of the issues discussed in this source is the Modbus protocol that lacks authentication, encryption, and encryption integrity.
One of the most useful and also dangerous features of Modbus is its ability to program controllers that many SG protocols share with Modbus. Due to this dangerous feature, attacker can use it to inject malware into PLCs and RTUs. One of the methods of intrusion detection in Modbus protocols is the use of model-based intrusion detection systems. Reference [6] introduces three model-based methods for monitoring and detecting Modbus TCP protocol attack. These methods provide a protection mechanism with respect to the topology and communication structure of the SCADA network. In order to prevent unauthorized access to the protected system, firewalls have been suggested as a security solution in many sources. One of its tasks is to block messages that are not structured in accordance with the protected area communication protocol [7].
Another common way to increase the security of communication protocols is to use cryptography. There are various traditional methods of encryption, but most are not usable in smart grid control systems. The reason is the limited computing power and low data transmission speed of these components, which must also meet the real-time performance requirements. These limitations make it difficult to implement sophisticated encryption. Reference [8] has explored various encryption methods to ensure data confidentiality and integrity.
3-2- Control equipment vulnerabilities
Many cyberattacks on industrial control systems have been exploited to exploit vulnerabilities in control equipment, one of which is the Stuxnet attack. Therefore, identification of these vulnerabilities is one of the issues of interest to researchers in this field [9]. In recent years, in addition to software vulnerabilities, various types of hardware have also been heavily favored by security experts. These are widespread in processors and electronic components and are found even on telecommunication surfaces [10].
In an effort to counteract this attack, the source proposes two security measures for the power grid state estimator, which is actually a measure of the minimum amount of attacker effort required to successfully execute an attack. These scales depend on the physical topology of the power grid and the degree of availability of the sensor outputs. Reference [14] stated that complete encryption and out-of-the-box protection of all equipment is not cost-effective and enforceable, and that the success of the injection attack can be prevented by protecting a limited number of measurements and their output.The number of these measurements is equal to the number of system state variables. In reference [15], two algorithms offer protection for a limited number of devices in such a way as to provide maximum security against injection attacks. Reference [16] first described an optimal attack strategy that can cause maximum damage to the system, and then by formulating the defense problem, it has been able to develop an optimal defense strategy and minimize the amount of damage. The economic effects of the data injection attack on the electricity grid market performance were formulated in paper [17].
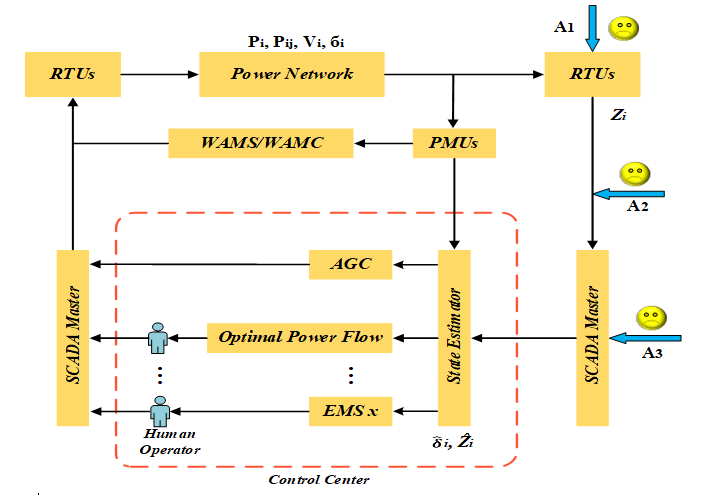
3-3-2- Attack on power grid state estimator and wrong data injection
The purpose of the power grid state estimator is to estimate the state variables of that system based on the measured data. In reference [18], the control center of the state system matrix of the variables was described. Inappropriate estimates can be due to various reasons, such as measurement failures or malicious attacks. In this scenario, it is assumed that the attacker knows the state matrix variables of the target power system and makes subversive measurements with knowledge of this matrix. It then injects these erroneous measurements into the control system to disrupt the state estimation process. Figure 3 provides a schematic overview of the data injection attack on power grid control system.
Figure 3. Schematic overview of the data injection attack on power grid control system
3-3-3- Invalid dynamic data injection attack
The attack attempts to inject the wrong data dynamically and create an unstable and invisible fashion in the system. Reference [19] assumed that the attacker's purpose is to inject the wrong data, destabilize the system, and remain secret. The author used the Kalman filter and the linear–quadratic–Gaussian (LQG) controller to monitor and control the discontinuous linear system over time, as well as to detect the attack of a false dynamic data injection. Finally, this article described the requirements for a successful attack and proposes a method to counter attack based on the use of plug-in sensors.
3-3-4- Information recovery attack
One of the most dangerous attacks is the information recovery attack. As observed in the "data injection" attacks, if the attacker can access the sensor or operator output data, he can enter the wrong data in an intelligent and purposeful manner, or accidentally, and control Error making the receiver [20]. In an information recovery attack, the attacker records the sensor or operator information under normal system conditions and sends it to the control network at the time of the attack and sabotage [21]. As such, the control system is cleverly deceived and, in addition to the loop control, the system goes into danger. One way to counter this attack is to add a Gaussian random input with a mean of zero to the system input [22]. Random input is an authentication signal and it is attempted to be optimally designed to minimize impact on system performance.
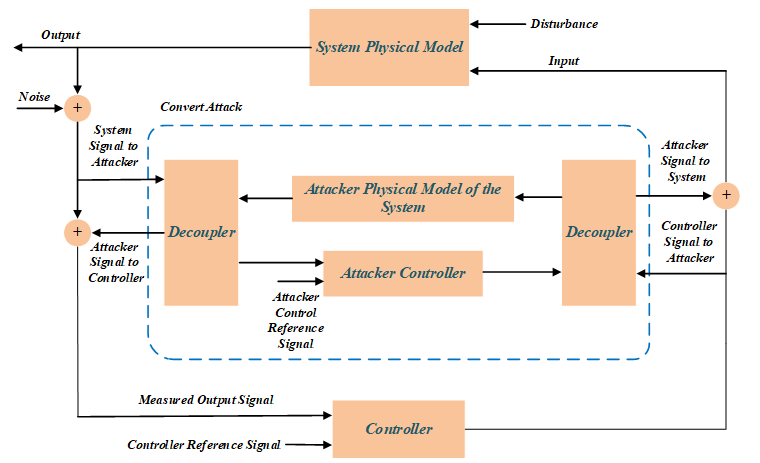
3-3-5- Stealth attack
The attack is actually a closed-loop information reconstruction attack. In other words, the attack output is reconstructed as a closed loop to eliminate the effect on the sensor output and keep the attack hidden. In these kinds of attacks, attacker should have a thorough understanding of the physical model of the system under control in order to simulate a model similar to it. As shown in Figure 4, the attacker puts the simulated model and its controller between the system and the master controller; and by sending arbitrary signals to the main controller input, it hides the attack and replaces the arbitrary work point.
Figure 4. Block diagram of stealth attack on power grid control system
4- Improving Cyber Security Management In SG Control Systems To Enhance Resilience Of Power Control Systems
In order to achieve optimal security, in addition to using appropriate security strategies there must be good security management. Appropriate security management tools include security policies, strategies, and programs that are based on accurate threat and risk analysis. In other words, given the wide range of cyber threats that industrial control systems are exposed to, it is essential to identify and analyze these threats to provide an optimal and cost-effective safeguard strategy. In general, the field of study of the articles in this section can be categorized as follows:
- Providing methods for identifying cyber threats and assessing their risks in industrial control systems
- Considering such analysis and evaluations to extract and select the optimal and cost-effective defense strategy and formulate a security plan
Much effort has been made to provide methods for identifying threats and risks as well as analyzing them in industrial control systems. In reference [23], it is attempted to estimate the security threats of cyber-physical systems using the game theory method.
5- Conclusion
In addition to exploiting unknown vulnerabilities, cyber attackers are developing more sophisticated methods to attack smart grid control systems. Thus, after going through IT-based security strategies, they are virtually confronted with a control system without security protections. On the other hand, the ultimate goal of attackers is to damage and disrupt the optimal functioning of the physical system under control, which is ignored in IT-based security strategies. It can only be stated that IT-based security strategies alone cannot provide a depth defense strategy (the in-depth defense strategy allows the attacker to pass through each layer again to a security layer that eliminates Designed to reduce the attack (or reduce its impact) to control systems. Therefore, this article identified various vulnerabilities and scenarios of cyber-attack in smart grid control systems so as to increase system resilience of power system and to reduce the effects of such attacks.
References
[1] S. Amin, "On cyber security for networked control systems," UC Berkeley, 2011.
[2] M. Ghiasi, "Detailed study, multi-objective optimization, and design of an AC-DC smart microgrid with hybrid renewable energy resources," Energy, vol. 169, pp. 496-507, 2019.
[3] D. J. Teumim, Industrial network security: Isa, 2010.
[4] V. M. Igure, S. A. Laughter, and R. D. Williams, "Security issues in SCADA networks," computers & security, vol. 25, pp. 498-506, 2006.
[5] B. Wang, M. Dabbaghjamanesh, A. K. Fard, and S. Mehraeen, "Cybersecurity Enhancement of Power Trading Within the Networked Microgrids Based on Blockchain and Directed Acylic Graph Approach," IEEE Transactions on Industry Applications, 2019.
[6] S. Cheung, B. Dutertre, M. Fong, U. Lindqvist, K. Skinner, and A. Valdes, "Using model-based intrusion detection for SCADA networks," in Proceedings of the SCADA security scientific symposium, 2007, pp. 1-12.
[7] Y. Chen, J. Hong, and C.-C. Liu, "Modeling of intrusion and defense for assessment of cyber security at power substations," IEEE Transactions on Smart Grid, vol. 9, pp. 2541-2552, 2016.
[8] D. Puthal, X. Wu, S. Nepal, R. Ranjan, and J. Chen, "SEEN: A selective encryption method to ensure confidentiality for big sensing data streams," IEEE Transactions on Big Data, 2017.
[9] Y. Xu, Y. Yang, T. Li, J. Ju, and Q. Wang, "Review on cyber vulnerabilities of communication protocols in industrial control systems," in 2017 IEEE Conference on Energy Internet and Energy System Integration (EI2), 2017, pp. 1-6.
[10] R. Arghandeh, A. von Meier, L. Mehrmanesh, and L. Mili, "On the definition of cyber-physical resilience in power systems," Renewable and Sustainable Energy Reviews, vol. 58, pp. 1060-1069, 2016/05/01/ 2016.
[11] R. Deng, P. Zhuang, and H. Liang, "False data injection attacks against state estimation in power distribution systems," IEEE Transactions on Smart Grid, vol. 10, pp. 2871-2881, 2018.
[12] A. Teixeira, S. Amin, H. Sandberg, K. H. Johansson, and S. S. Sastry, "Cyber security analysis of state estimators in electric power systems," in 49th IEEE conference on decision and control (CDC), 2010, pp. 5991-5998.
[13] X. Liu and Z. Li, "Local load redistribution attacks in power systems with incomplete network information," IEEE Transactions on Smart Grid, vol. 5, pp. 1665-1676, 2014.
[14] R. B. Bobba, K. M. Rogers, Q. Wang, H. Khurana, K. Nahrstedt, and T. J. Overbye, "Detecting false data injection attacks on dc state estimation," in Preprints of the First Workshop on Secure Control Systems, CPSWEEK, 2010.
[15] G. Dan and H. Sandberg, "Stealth attacks and protection schemes for state estimators in power systems," in 2010 First IEEE International Conference on Smart Grid Communications, 2010, pp. 214-219.
[16] Q. Yang, J. Yang, W. Yu, D. An, N. Zhang, and W. Zhao, "On false data-injection attacks against power system state estimation: Modeling and countermeasures," IEEE Transactions on Parallel and Distributed Systems, vol. 25, pp. 717-729, 2013.
[17] L. Xie, Y. Mo, and B. Sinopoli, "Integrity data attacks in power market operations," IEEE Transactions on Smart Grid, vol. 2, pp. 659-666, 2011.
[18] A. Monticelli, State estimation in electric power systems: a generalized approach: Springer Science & Business Media, 2012.
[19] K. Manandhar, X. Cao, F. Hu, and Y. Liu, "Detection of faults and attacks including false data injection attack in smart grid using Kalman filter," IEEE transactions on control of network systems, vol. 1, pp. 370-379, 2014.
[20] Y. Mo and B. Sinopoli, "Secure control against replay attacks," in 2009 47th annual Allerton conference on communication, control, and computing (Allerton), 2009, pp. 911-918.
[21] M. H. Amini, H. Arasteh, and P. Siano, "Sustainable Smart Cities Through the Lens of Complex Interdependent Infrastructures: Panorama and State-of-the-art," in Sustainable Interdependent Networks II: From Smart Power Grids to Intelligent Transportation Networks, M. H. Amini, K. G. Boroojeni, S. S. Iyengar, P. M. Pardalos, F. Blaabjerg, and A. M. Madni, Eds., ed Cham: Springer International Publishing, 2019, pp. 45-68.
[22] S. Mehrdad, S. Mousavian, G. Madraki, and Y. Dvorkin, "Cyber-physical resilience of electrical power systems against malicious attacks: A review," Current Sustainable/Renewable Energy Reports, vol. 5, pp. 14-22, 2018.
[23] S. Amin, G. A. Schwartz, and A. Hussain, "In quest of benchmarking security risks to cyber-physical systems," IEEE Network, vol. 27, pp. 19-24, 2013.
For a downloadable copy of March 2020 eNewsletter which includes this article, please visit the IEEE Smart Grid Resource Center.

Mohammad Ghiasi is currently a Research Assistant at the Shiraz University of Technology. He received his B.S. degree from IAU-South Tehran Branch in 2012 and M.S. degree from IAU-Science and Research Branch in 2016, both in electrical power engineering. Since 2007 he has been with the Power Control Center (PCC) of Tehran Metro as a senior control power engineer. He is a member of Tehran Construction Engineering Organization (TCEO), and also a member of IEEE. His research on modeling, simulation and optimization of power systems, integration and control of hybrid and distributed renewable energy resources, smart grids, resiliency and cyber security in power systems has led to multiple publications in these fields.

Moslem Dehghani was born in Shiraz, Iran, in 1990. He received B.S. and M.S. degrees in Electrical Engineering from Islamic Azad University-kareroun branch respectively in 2012 and 2014, and he has started studying in Ph.D degree in Electrical Engineering in 2019 at Shiraz University of Technology, Shiraz, Iran. His current research interests include power electronic, control, and cyber security analysis of smart grids, microgrid, smart city as well as protection of power systems, fuzzy logic and signal processing.

Abdollah Kavousi-Fard received the B.Sc. degree from Shiraz University of Technology, Shiraz, Iran, in 2009; the M.Sc. degree from Shiraz University, Shiraz, in 2011; and the Ph.D. degree from Shiraz University of Technology, Shiraz, Iran, in 2016, all in electrical engineering. He was a Postdoctoral Research Assistant at the University of Michigan, Mi, USA from 2016-2018. Dr. Kavousi-Fard was a researcher with the University of Denver, Denver, CO, USA from 2015 to 2016 conducting research on microgrids. He is currently an assistant professor at Shiraz University of Technology, Shiraz, Iran. His current research interests include operation, management and cyber security analysis of smart grids, microgrid, smart city, electric vehicles as well as protection of power systems, reliability, artificial intelligence and machine learning. Dr Kavousi-Fard is an Editor in Springer, ISTE ISI journal.
To have the Bulletin delivered monthly to your inbox, join the IEEE Smart Grid Community.
Past Issues
To view archived articles, and issues, which deliver rich insight into the forces shaping the future of the smart grid. Older Bulletins (formerly eNewsletter) can be found here. To download full issues, visit the publications section of the IEEE Smart Grid Resource Center.