Ransomware: A Change Will Do Us Good
Written by Mike Prescher
I am frequently asked how it is that electric grids and other critical infrastructure have, in what seems like just a few years, become such a focus for ransomware attacks. My most succinct response is, “It’s become a target-rich environment.” The elements and systems which make up grid operations have been rapidly evolving from analog technology to digital-lots of change there. But have cybersecurity practitioners defending those grid operations changed along with this transition?
While serving very different business purposes, as with their Information Technology (IT) cousins, these digital Operational Technology (OT) systems change-frequently. They are henceforth subject to the same code-level and protocol behavior weaknesses and vulnerabilities all such logic systems are susceptible to. We must accept the fact that exploitable bugs in their various interfaces, functions and the underlying communication and security protocols, are going to be there.
In addition, today we have the advent of difficult-to-trace monetary transactions made possible by cryptocurrency. This on its own has enticed and enabled bad actors to go after bigger targets. And what’s worth a king's ransom? Electricity for millions of people, water, transportation, or the food chain. Monetary gain is not the only motivation. In the current global geo-political environment these bad actors may also be encouraged and even directly supported in their efforts by others who are after something different-power, control, or advantage for non-kinetic attack capabilities-the adversary nation state.
Lastly, and surely the most important, what about the grid operators themselves? Because of concerns for grid reliability, they have historically sought stability and rightly resisted rapid change unless it was deemed absolutely necessary. And here we are, systems made up of ever more complex digital elements: relays, sensors, HMI, circuit-breakers, et al. What grid sustainers and defenders end up with are very complex systems with a myriad of targets to protect, targets which are subject to continuous change and vulnerability. That’s about as tough a problem as any type of engineer could ask for.
We find some comfort in that in the U.S., we have a pretty good level of cooperation and coordination regarding cyber defense. This cooperation includes the usual alphabet soup: NERC, FERC, NIST, CISA, DoD, DoE, NSA and still others like the IEEE and their Cybersecurity & Privacy Standards Committee | IEEE Computer Society. Each contributes to cybersecurity preparedness in their own way. But while there is some good cooperation here and there, it’s another aspect of the Cyber Attack for Ransome (CAFR) challenge where some change might do us some good. More cooperation geared specifically to help operators in the field make effective use of it all, for threats like ransomware.
Certainly, in my own grid project work around ransomware response, solution delivery teams have found that something beyond the currently available frameworks, standards and specifications was needed, and it was distinctly non-digital in nature. Namely, a deeper understanding of the human operators and support personnel, and the operations process that depends on those increasingly complex systems.
While there has been plenty of attention paid to cyber hygiene technology, the human workflow and operation process remained relatively untouched. Considering effective ransomware responses, that’s a big miss, because cybersecurity hygiene can’t supply all that is required. One generic definition of classical cyber hygiene might be..
A set of technology-based practices focused on maintaining the digital health and security of an organization’s data, devices and networks. This can include digital information confidentiality, integrity and secure access, protecting data from potential cyber threats.
That definition translates to firewalls, network access control lists, application white-listing, anti-virus, intrusion detection, identity access management, etc. These protections are critical for ransomware attack resilience, but less so for an effective response. If we assume for the moment that nation state sponsored bad actors have been exploring and probing various grid operations for years (and they have), once a ransomware attack is underway and a clock on a computer screen is counting down, that’s not the time to try and figure out how they got in, nor is it time to hold all-day response planning meetings. If a grid cyber team is thinking that approach will work, they need to consider a change.
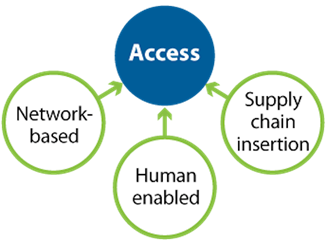
For an effective CAFR response, visible countdown timers and fear of the unknown are not your allies. Your best allies against the attack are a practical, practiced and intentionally uncomplex CAFR response plan ready to go, and pre-defined pre-approved triggers for when to enact it. The response mechanisms involved can reside within just three pillars of capability:
Achieving these capabilities typically does not require more cyber hygiene, but instead a better understanding of the organization’s communications networks (virtual and physical), and of the operations workflow and support processes. One of the best perspectives on cyber which emphasizes these aspects is from Idaho National Lab (INL) and detailed in a book authored by Andy Bochman and Sarah Freeman called "Countering Cyber Sabotage." While the INL methodology does not focus on specific types of cyberattacks, not surprisingly it aligns with and informs the Three Pillars capabilities including Isolation...
“…cyber-physical safeguards can be counted on to block the progress of an attack or, failing that, keep the high-value target safe from damage or destruction. Or limit the damage enough to allow restoration and continued operation even if in a degraded state.”
The Isolation in question requires well-designed tiered and modular standards-based data network architectures (physical and logical).
In total INL CCE methods define a deep analysis of critical infrastructure operations that go beyond, as they put it, “hope and hygiene.” They use a four phased sequential execution approach which you can read about in their book. Because this article is limited to ~1000 words, I’ll risk summarizing that book and the entire methodology with a single INL graphic:
For a successful CAFR response grid cyber teams and operators may need to consider a change in their current approach. They must pursue a much deeper understanding of their own operations while considering the data network design, human resources who perform the day-to-day business of operating a grid, and the suppliers and contractors who contribute components, software and services, all of them requiring some level of systems access. Remember, cyber hygiene is one half of the defend-respond equation; People and Process are the other, and both are required. With the Three Pillars capabilities in place, an effective CAFR response becomes achievable.
This article was edited by Binesh Kumar.
To view all articles in this issue, please go to November 2022 eBulletin. For a downloadable copy, please visit the IEEE Smart Grid Resource Center.

Mike Prescher, CISSP, CISA, CISM, serves as a Principal Architect within Black & Veatch’s Engineering & Development Services teams.
To have the Bulletin delivered monthly to your inbox, join the IEEE Smart Grid Community.
Past Issues
To view archived articles, and issues, which deliver rich insight into the forces shaping the future of the smart grid. Older Bulletins (formerly eNewsletter) can be found here. To download full issues, visit the publications section of the IEEE Smart Grid Resource Center.