The Cyber-Physical Security of the Power Grid
By Martin Molnár and István Vokony
Since critical infrastructures play a crucial role in our everyday life, its security has to be considered as one of the most important challenges in this modern era. The Internet of Things spreads in almost every segment of industry, hence these critical systems become more vulnerable to cyber-attacks and so do power grids. In 2009 to 2010 a well-protected and isolated Iranian uranium enrichment plant was attacked by a Stuxnet worm, and the most famous cyber-attack on a critical infrastructure was committed against the power grid in Kiev, Ukraine during 2015–2016.
Physical and cyber security of smart power grids is very difficult due to their complexity and inhomogeneity. A huge part of the system is connected to the Internet, hence remote control is possible. Industrial control systems (ICS) are applied in various forms, for example in power grids EMS/SCADA architectures are used (Görgey et al., 2019). A well-structured defense mechanism against cyber threats can only be effective if the whole power grid is deeply known by its ICS. For this reason, it is worth examining smart grid and SCADA structures integrated into each other. This approach can be effectively used in developing a new testbed for cyber-attack impact analysis against smart power grids. In this article, a new perspective is proposed of the smart power grid structure, and a modular testbed-like system for modeling cyber-attacks, anomaly and intrusion detection.
Optimized smart grid model
The literature approaches smart grid (SG) applications in two different ways. One approach considers the SG as a centralized cloud-based structure, while the other models SG in a modular way. Each architecture has its own advantages, so it is worth the effort to compare them.
As it is seen in Figure 1, in the centralized model the grid control appears as an independent service unit alongside generation, transmission, distribution, and different types of load. It demonstrates that cloud-based databases and distributed applications play a huge role in the proper operation of the grid. On the other hand, however, it simplifies the complexity of the system, which has several drawbacks and makes the model unrealistic. In contrast, the layered architecture makes it possible to analyze smart grids in a modular way (see Figure 2); consequently, a hierarchical structure can be examined without getting rid of the system’s complexity.
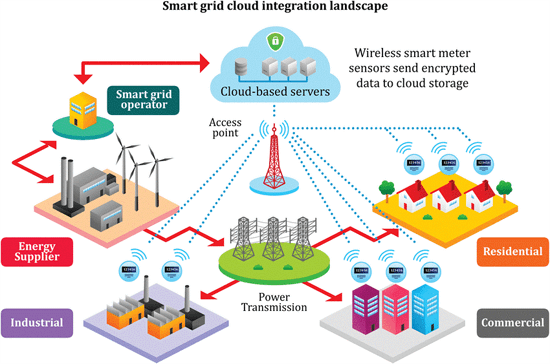
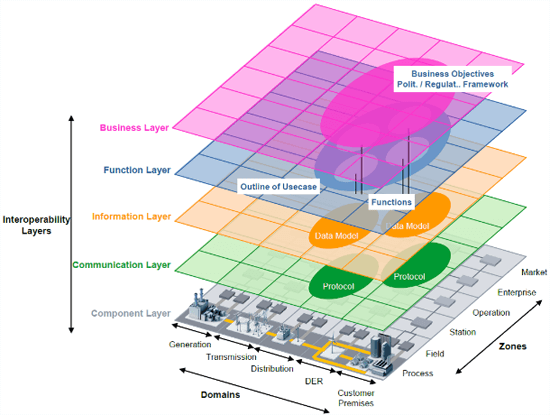
Figure 1: Centralized SG structure (Khalil et al., 2017) Figure 2: Layered SG architecture (Energy N. et al., 2018)
Using the latter architecture, experts can clearly model every layer of the system with integrated control automation. This method allows for the examination of the whole power grid in one big complex unit, which is broken down into several smaller functional layers.
Smart grid and SCADA integration
The power grid is supplemented with several IT applications; hence computer support plays an important role in grid control automation. Based on the IT supports functionality and complexity, two types of support systems can be distinguished. The SCADA (Supervisory Control and Data Acquisition) is a distributed architecture that is responsible for data collection and system control. On the contrary, the EMS (Energy Management System) is a system that provides all the necessary data management and calculations. In terms of the research, SCADA systems are the key to creating a connection to the whole smart power grid. SCADA architectures can be broken down into 5 levels, which automatically implies the motivation for SG integration. Comparing its structure with the modular smart grid model, the SCADA components can obviously be classified into the layers of SG.
The SG’s component layer includes the SCADA’s physical subsystem and all the network operation devices like switches and bridges. The communication layer contains every protocol and standard with which the network connections are built and operated. As SCADA systems manage huge amounts of data, a comfortable and effective storage option is necessary. Besides smart grids, these also generally use cloud-based database structures which are the part of the information/data layer. The function layer consists of all the calculations, operations and control logic that are responsible for the controllability of the system. SCADA provides real-time user intervention, hence human-machine and graphical interfaces at the end systems are usually applied. These together belong to the highest SG level, the business layer. All these classifications and considerations are going to play a key role in constructing a new complex testbed.
Cybersecurity issues and solution considerations
For an effective defensive strategy, the possible cyber-attack structures have to be well-known. Unfortunately, there is a huge amount of attack types, and they are evolving all the time. In addition, new attacks are likely to be made very easily since combining them is very simple yet effective way of creating more harmful ones. This is the main reason for the attack modeling to play such an important role in a proper defense system. The attacking-tree is a well-known and widely used attack model, as it enables to break an attack down into smaller sub-attack units (Rodofile et al., 2019, Kalluri et al., 2016). Therefore, experts can get enough information about the structure and the goals of the attack, which improves the chances for a better defense system to be applied. Otherwise, this model provides no information about the deeper mechanism of the attack, but for the purposes of the present research it is enough to understand their structure and the impact they make on the power grid. This method is going provide all the necessary information about the attacks’ sub-goals and the system parts they exert their effects on.
Since there is a huge variety of different attack types smart power grids have to face, elimination is not a proper approach for defense. Rather, prevention is considered to be the most effective defensive strategy. The goal, instead of understanding how all the attacks work, is to detect every single anomaly or later on, intrusion in the system, so the attacks cannot exert their impact. Interestingly, during the two attacks mentioned above, the intrusion had happened much earlier than the damage was caused. From this fact, the conclusion can be drawn that anomaly and intrusion detection is the best possible way to avoid the destruction caused by cyber-attacks (Sun et al., 2018).
Testbed for Intrusion and Anomaly Detection Systems
The complexity of smart power grids makes it almost impossible to model them in a deeply detailed way. These systems have physical components, communication networks and functional operations, and since they are all much diverse, it is a huge challenge to develop a proper framework. In this research, considering the integrated SCADA and SG structure presented above, a new approach for a testbed will be proposed. This framework must be complex enough to represent the system properly, yet simple and transparent for comfortable work. The testbed is going to demonstrate how an attack against the smart grid behaves. Using the attacking-tree model, the system is going to monitor the way of the attack, so intrusions and anomalies can be examined at any condition. Considering this type of approach, people will be able to understand the attacks and analyze their impact step-by-step.
The platform is still under development and hasn’t been finished yet but is already able to demonstrate it’s operation. The software includes two databases - one for the attacks, and one for the system components. The attacks can be broken into sub attacks using the tree-model, of which all of them can be built up. The attributes of them are: the entry point, the targeted component and their function. The components are stored based on their system-level, communication-type and co-operating components. The program connects these two databases, models the power grid, simulates the attacks and operates the graphical user interface. The main functions are the routing and impact-analysis, of which the former is demonstrated on an example below.
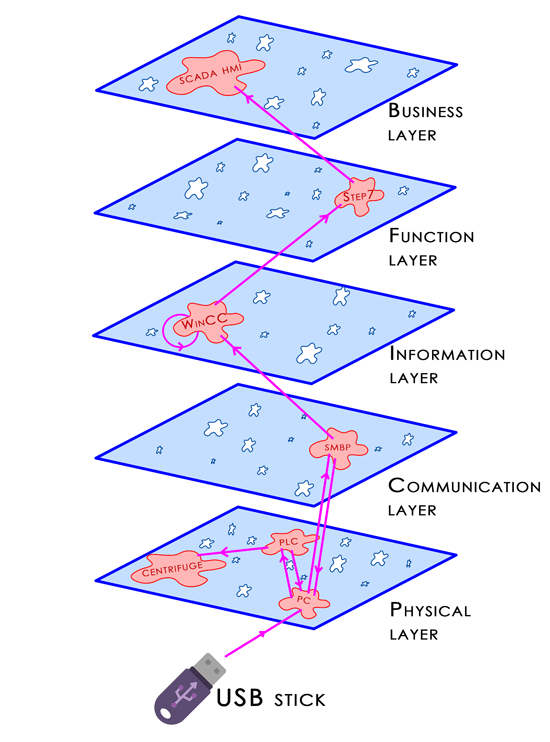
Figure 3: Stuxnet routing simulation
On the upper figure operation of the routing function can be seen. This example shows the Iranian Stuxnet attack’s entry point and route in the cyber-physical system up until hijacking of the centrifuges. In this testbed the weaknesses of the grid can be pointed out, and with simulation of an experimental attack, the security, robustness and reliability of the system can be increased.
For a downloadable copy of November 2019 eNewsletter which includes this article, please visit the IEEE Smart Grid Resource Center.
Contributors:

Martin Molnar is a third-year electrical engineer at the hungarian Budapest University of Technologies and Economics. Besides his studies he is the vice president of the Student Association of Energy where he is responsible for internal programs, the soft-skills and the professional development of members. Since he is into informatics, he has always desired to do his own research somewhere in-between IT and energetics, so he has started to work on his theme - cyber-physcial security of the power grid - early summer. He is also down to topics like smart grids, microgrids, system operation and renewable integration. This summer he became a member of the Hungarian Electrotechnical Association that has started a collaboration called SeConSyS for the cyber-physical security of the hungarian power grid. In the near future he will also join its Workgroup Technology to help their work and to operate the projects support interface.

Dr. István Vokony was born in 1983. He received M.Sc. degree in electrical engineering and obtained his Ph.D. degree from Budapest University of Technology and Economics in 2007 and 2012, respectively. He is working as an enterprise architect at E.ON Business Services Hungary at Department of Strategy and Architecture Business IT. He is a part-time senior lecturer and researcher at the Department of Electric Power Engineering, Budapest University of Technology and Economics. His fields of interest include power system stability analysis, renewable system integration, energy storage and smart grids.
To have the Bulletin delivered monthly to your inbox, join the IEEE Smart Grid Community.
Past Issues
To view archived articles, and issues, which deliver rich insight into the forces shaping the future of the smart grid. Older Bulletins (formerly eNewsletter) can be found here. To download full issues, visit the publications section of the IEEE Smart Grid Resource Center.




